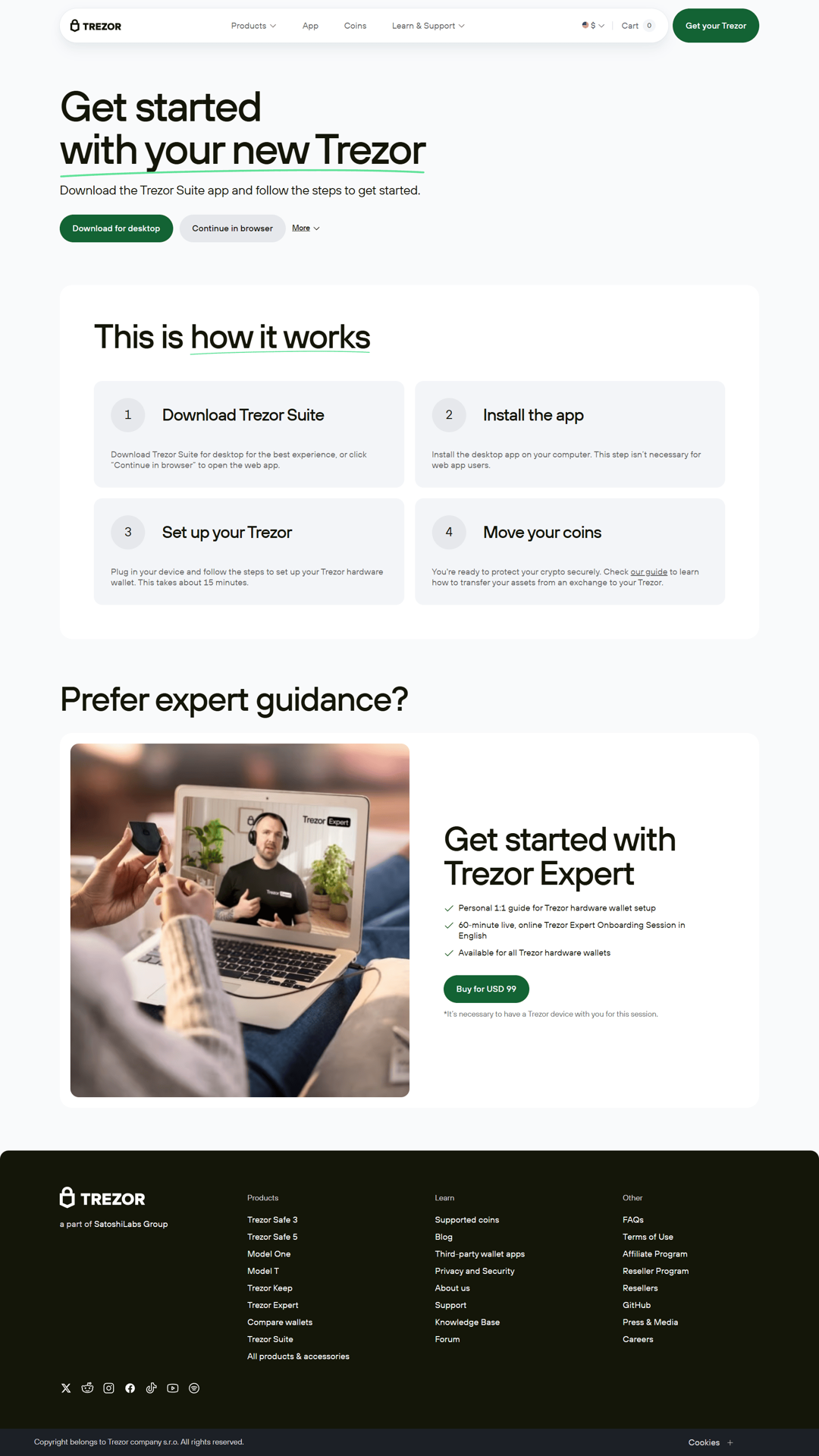
Introduction to Trezor Login
Trezor Login is the gateway to securely managing your cryptocurrency assets using the Trezor hardware wallet and its companion software, Trezor Suite. Designed with user security and ease of access in mind, Trezor Login ensures that your digital assets remain protected from online threats while providing a seamless experience for both beginners and advanced users. This comprehensive guide explores the process of accessing your Trezor wallet, setting up your device, and utilizing the Trezor Login system to manage your cryptocurrencies effectively. Whether you're new to the crypto space or a seasoned investor, Trezor Login offers a robust solution for safeguarding and organizing your digital wealth.
What is Trezor Login?
Trezor Login refers to the process of accessing your Trezor hardware wallet through the Trezor Suite application or compatible third-party platforms. The Trezor hardware wallet is a physical device that stores your private keys offline, protecting your cryptocurrencies from hacks, malware, and unauthorized access. By using Trezor Login, you can interact with your wallet to view balances, send transactions, and manage multiple cryptocurrency accounts in a secure environment. The Trezor Login system prioritizes user control, ensuring that your funds remain safe even in the event of a compromised computer or network.
The Trezor Login process begins with connecting your Trezor device to a computer or mobile device and unlocking it with a PIN. For enhanced security, users can enable a passphrase to create hidden wallets, adding an additional layer of protection. Trezor Login is designed to be intuitive, allowing you to manage your assets with confidence, whether you're trading, storing, or transferring cryptocurrencies.
Why Choose Trezor Login for Cryptocurrency Management?
Choosing Trezor Login for managing your cryptocurrencies offers unmatched security and flexibility. Unlike software wallets that store private keys on potentially vulnerable devices, Trezor Login leverages the offline storage of a hardware wallet to keep your assets safe from online threats. The Trezor device ensures that your private keys never leave the device, even during transactions, making it nearly impossible for hackers to gain access without physical possession of the device and your credentials.
Additionally, Trezor Login through Trezor Suite provides a user-friendly interface that simplifies complex cryptocurrency tasks. You can manage multiple accounts for different cryptocurrencies, track your portfolio, and execute transactions with ease. The Trezor Login system also supports advanced privacy features, such as the ability to create multiple accounts with unique extended public keys (XPUBs) to enhance transaction privacy. By choosing Trezor Login, you gain peace of mind knowing that your digital assets are protected by industry-leading security standards.
Setting Up Your Trezor Device for Trezor Login
Initial Setup Process
To begin using Trezor Login, you must first set up your Trezor hardware wallet. Start by unboxing your Trezor device and connecting it to your computer or mobile device using the provided USB cable. Download and install the Trezor Suite application from the official source to ensure authenticity. Once installed, open Trezor Suite and follow the on-screen instructions to initialize your device. This process involves creating a new wallet or recovering an existing one using a seed phrase.
During setup, your Trezor device generates a random seed phrase, a string of words that serves as the master key to your wallet. This seed phrase is critical for recovering your funds if your device is lost, stolen, or damaged. Write down the seed phrase on the provided recovery card and store it in a secure location, separate from your Trezor device. Never store the seed phrase digitally, as this increases the risk of exposure to hackers.
Configuring Your PIN
After generating the seed phrase, you’ll be prompted to set a PIN for your Trezor device. This PIN is required every time you access Trezor Login, adding a layer of security to prevent unauthorized access. Choose a strong PIN that is difficult to guess but easy for you to remember. The Trezor device randomizes the PIN entry pad on its screen, making it resistant to keyloggers or shoulder-surfing attacks. Once the PIN is set, your device is ready for Trezor Login.
Enabling Passphrase Protection
For advanced users, Trezor Login supports an optional passphrase feature that creates hidden wallets for added security. A passphrase is a user-defined word or phrase that, when combined with your seed phrase, generates a unique wallet. Each passphrase creates a completely separate wallet, meaning that even if someone gains access to your seed phrase, they cannot access your funds without the correct passphrase. To enable this feature, navigate to the Device Settings in Trezor Suite and toggle on the passphrase option. Be sure to write down your passphrase and store it securely, as losing it will result in permanent loss of access to the associated wallet.
Accessing Trezor Login
Using Trezor Suite
The primary method for Trezor Login is through the Trezor Suite application. After setting up your device, connect it to your computer and open Trezor Suite. The application will prompt you to enter your PIN on the Trezor device. If you’ve enabled passphrase protection, you’ll also need to enter your passphrase. Once authenticated, Trezor Suite displays your portfolio, including a breakdown of your assets and individual cryptocurrency accounts. From here, you can view balances, send or receive funds, and manage your accounts.
Trezor Suite’s intuitive interface makes Trezor Login accessible to users of all experience levels. The dashboard provides a portfolio overview, showing the total value of your assets and recent transactions. You can select specific cryptocurrencies from the left-hand menu to view detailed account information, including transaction history and addresses. Trezor Login via Trezor Suite also supports features like buying, selling, and swapping cryptocurrencies directly within the app, making it a comprehensive tool for crypto management.
Using Trezor Connect for Third-Party Applications
In addition to Trezor Suite, Trezor Login can be used with third-party applications through Trezor Connect, a platform that enables secure integration with external services. Trezor Connect allows you to authenticate transactions and access your wallet through compatible wallets like MetaMask or Electrum. To use Trezor Login with Trezor Connect, connect your Trezor device to your computer, open the third-party application, and select Trezor as your wallet. You’ll be prompted to enter your PIN and, if applicable, your passphrase on the Trezor device to authorize access.
This feature makes Trezor Login versatile, allowing you to interact with decentralized applications (dApps) and other platforms while maintaining the security of your hardware wallet. By using Trezor Connect, you can manage your assets across multiple platforms without compromising security, as all transaction signing occurs on the Trezor device itself.
Managing Accounts with Trezor Login
Creating and Organizing Accounts
Trezor Login through Trezor Suite allows you to manage multiple accounts for each supported cryptocurrency. Each account is a collection of addresses linked to a unique extended public key (XPUB), which enhances privacy by keeping transactions from different accounts separate. To create a new account, navigate to the Accounts section in Trezor Suite and select the desired cryptocurrency. Click the option to add a new account, and Trezor Suite will generate a new set of addresses for that account.
You can label accounts for specific purposes, such as savings, daily expenses, or trading, to keep your portfolio organized. This feature is particularly useful for advanced users who want to maintain separate accounts for privacy or accounting purposes. Trezor Login makes it easy to switch between accounts, ensuring that all transactions are linked to the correct account.
Standard vs. Legacy Accounts
When using Trezor Login, you may encounter standard and legacy accounts for certain cryptocurrencies, particularly those with SegWit support, such as Bitcoin. Standard accounts use modern address formats that offer improved efficiency and lower transaction fees. Legacy accounts, on the other hand, use older address formats that may still hold funds from past transactions. While standard accounts are recommended, you can continue using legacy accounts or transfer funds to a standard account by sending a transaction within Trezor Suite.
Enhancing Privacy with Multiple Accounts
One of the key benefits of Trezor Login is the ability to enhance transaction privacy by using multiple accounts. Each account has its own XPUB, meaning that transactions from one account cannot be easily linked to another. This is particularly useful for users who want to protect their financial privacy by segregating transactions for different purposes. However, be cautious when sending funds between accounts, as frequent transfers may indicate common ownership, reducing the privacy benefits.
Security Features of Trezor Login
Offline Key Storage
The cornerstone of Trezor Login’s security is the offline storage of private keys on the Trezor hardware wallet. Unlike software wallets that store keys on a connected device, the Trezor device keeps your keys isolated from the internet, making them immune to online hacks. During Trezor Login, all transaction signing occurs on the device itself, ensuring that your private keys never leave the secure environment.
PIN and Passphrase Protection
The Trezor Login process requires a PIN to unlock the device, preventing unauthorized access even if the device is stolen. The randomized PIN pad on the Trezor device’s screen adds an extra layer of protection against keyloggers. For users who enable passphrase protection, Trezor Login becomes even more secure, as each passphrase creates a unique hidden wallet that cannot be accessed without the correct passphrase.
Firmware Authentication
To ensure the integrity of your Trezor Login, Trezor devices require firmware authentication during setup and updates. This process verifies that the device is running genuine firmware, protecting against compromised or malicious software. Always download firmware updates through the official Trezor Suite application to maintain the security of your Trezor Login.
Recovery Options
In the event of a lost, stolen, or damaged Trezor device, Trezor Login allows you to recover your funds using your seed phrase and, if applicable, your passphrase. By entering the seed phrase into a new Trezor device or compatible software, you can regain access to your accounts. Trezor Login ensures that your funds remain accessible as long as you have your recovery credentials, making it a reliable solution for long-term crypto storage.
Troubleshooting Common Trezor Login Issues
Forgotten PIN
If you forget your PIN, you cannot access Trezor Login directly, but your funds remain safe as long as you have your seed phrase. To regain access, reset your Trezor device and recover your wallet using the seed phrase. During recovery, you’ll set a new PIN. Be aware that resetting the device erases its current configuration, so always keep your seed phrase secure.
Passphrase Errors
Passphrase errors are a common issue during Trezor Login, as passphrases are case-sensitive and must be entered exactly as set. If you enter an incorrect passphrase, you’ll access a different hidden wallet or an empty one. Double-check your passphrase for accuracy, including spaces and capitalization. If you’ve lost your passphrase, you’ll need to rely on a backup copy or a hint you created during setup, as Trezor cannot recover lost passphrases.
Device Connection Issues
If Trezor Suite fails to detect your device during Trezor Login, ensure that the USB cable is securely connected and try a different port or cable. Verify that you’re using the latest version of Trezor Suite and that your device’s firmware is up to date. If issues persist, consult the Trezor support resources for detailed troubleshooting steps.
Advanced Features of Trezor Login
Integration with Full Nodes
For users seeking maximum control and privacy, Trezor Login supports connecting to your own full node. This allows you to verify transactions independently without relying on third-party servers, enhancing both security and self-sovereignty. Configure this feature in Trezor Suite’s settings to connect to your node, ensuring that your Trezor Login experience is fully decentralized.
Hiding Sensitive Information
Trezor Login includes features to protect your sensitive information from potential eavesdroppers. Trezor Suite allows you to blur scam airdrop tokens and sort them into a hidden section, reducing the risk of interacting with fraudulent assets. Additionally, you can manage your portfolio in view-only mode on mobile devices, keeping your balances private in public settings.
Multi-Language Support
To cater to a global audience, Trezor Login via Trezor Suite supports a wide range of languages. You can select your preferred language in the application settings, making it easier to manage your assets in a familiar interface. This feature ensures that Trezor Login is accessible to users worldwide, regardless of their native language.
Best Practices for Secure Trezor Login
To maximize the security of your Trezor Login, follow these best practices. Always store your seed phrase and passphrase in secure, offline locations, such as a safe or a safety deposit box. Avoid sharing your recovery credentials with anyone, and never enter them into a computer or mobile device unless you’re recovering your wallet. Regularly update your Trezor device’s firmware to protect against vulnerabilities. When using Trezor Login in public or on shared devices, ensure that no one can see your PIN or passphrase entry. Finally, consider using a VPN or Tor to mask your IP address when accessing Trezor Login, further enhancing your privacy.
Frequently Asked Questions About Trezor Login
What is Trezor Login and how does it work?
Trezor Login is the process of accessing your Trezor hardware wallet through Trezor Suite or compatible third-party applications. Connect your Trezor device, enter your PIN, and, if enabled, your passphrase to manage your cryptocurrencies securely.
Is Trezor Login safe to use?
Yes, Trezor Login is highly secure, as private keys remain on the offline Trezor device. The PIN and optional passphrase add additional layers of protection, making unauthorized access nearly impossible.
Can I use Trezor Login without Trezor Suite?
Yes, Trezor Login can be used with third-party applications via Trezor Connect, such as MetaMask or Electrum, allowing secure integration with external platforms.
What happens if I forget my PIN for Trezor Login?
If you forget your PIN, you can reset your Trezor device and recover your wallet using your seed phrase. You’ll set a new PIN during the recovery process.
How does the passphrase feature enhance Trezor Login security?
The passphrase creates hidden wallets that require both the seed phrase and the passphrase to access. This ensures that even if your seed phrase is compromised, your funds remain secure without the passphrase.
Can someone access my funds with just my Trezor device and PIN?
If you use a standard wallet without a passphrase, someone with your device and PIN could access your funds through Trezor Login. Using a passphrase-protected hidden wallet prevents this.
How do I recover my wallet if my Trezor device is lost?
With your seed phrase and, if applicable, your passphrase, you can recover your wallet on a new Trezor device or compatible software via Trezor Login.
Does Trezor Login support all cryptocurrencies?
Trezor Login supports a wide range of cryptocurrencies through Trezor Suite, including Bitcoin, Ethereum, and many others. Check the official Trezor documentation for a full list.
Can I use Trezor Login on my mobile device?
Yes, Trezor Login is available on mobile devices through the Trezor Suite app, which offers full functionality on Android and view-only mode on iOS.
How do I update my Trezor device for secure Trezor Login?
Connect your Trezor device to Trezor Suite, and the application will prompt you to update the firmware if a new version is available. Follow the instructions to ensure secure Trezor Login.
Disclaimer
The information provided in this guide is for educational purposes only and should not be considered financial or investment advice. Always verify the authenticity of software and firmware used with Trezor Login to avoid security risks. Store your seed phrase and passphrase securely, as loss of these credentials may result in permanent loss of access to your funds. Consult official Trezor resources or support for specific issues or updates related to Trezor Login.
Made in Typedream